In today’s fast-paced digital landscape, cybersecurity threats evolve rapidly. To stay ahead of these threats, automating incident alerts and responses has become essential. By integrating EDR (Endpoint Detection and Response) and SOAR (Security Orchestration, Automation, and Response) technologies, organizations can reduce the time it takes to detect and respond to security incidents, ultimately minimizing potential damage.
In this post, I’ll walk you through how I set up an automated incident alert and instant response system using the principles of EDR and SOAR, ensuring rapid and efficient threat management.
Overview of the wrokflow :
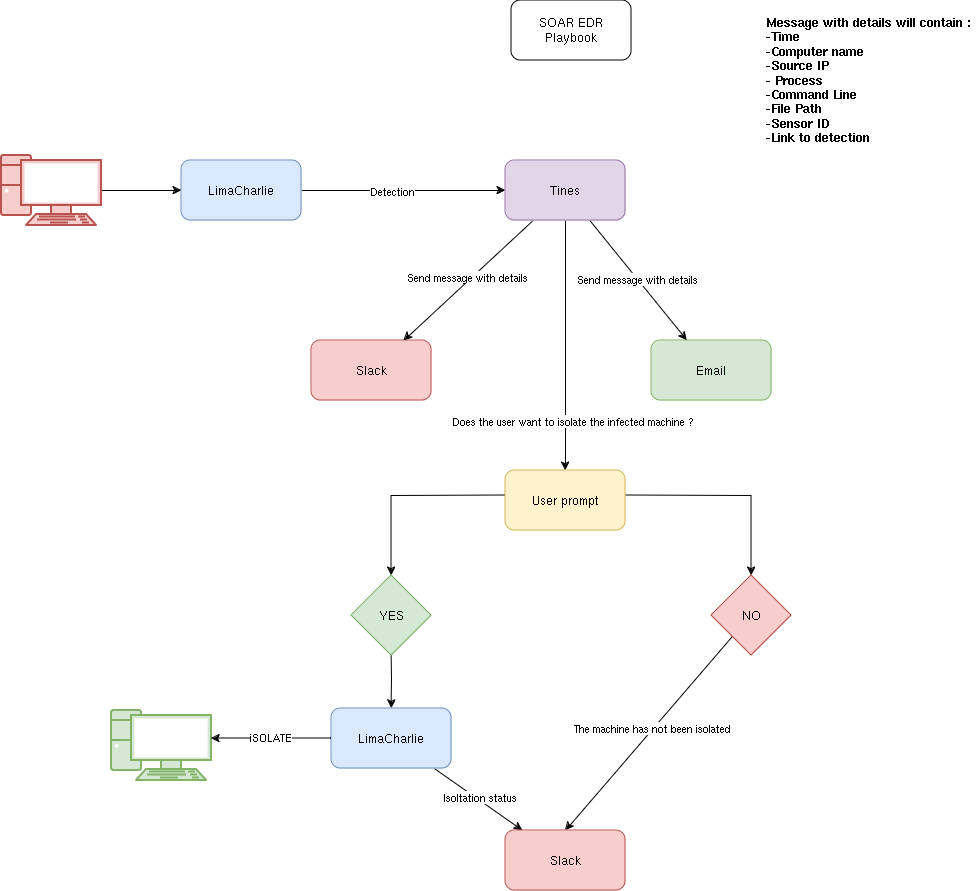
So In this setup, we have three main components:
- Endpoint: A Windows machine, which is the system being monitored.
- EDR (LimaCharlie): The EDR flags suspicious activity based on predefined Sigma rules. These rules detect abnormal behavior on the Windows machine.
- SOAR (Tines): Tines automates the response workflow.
Process:
- The Windows machine is connected to LimaCharlie, which monitors for suspicious activity.
- When a Sigma rule is triggered, LimaCharlie flags the incident and forwards the information to Tines.
- Tines is integrated with both email and Slack. It sends a user prompt asking whether to isolate the machine.
- If the response is “Yes”:
- Tines sends a confirmation message to Slack and executes a command via the LimaCharlie API to isolate the machine.
- If the response is “No”:
- Tines simply informs the user of the decision, and no further action is taken.
- This workflow automates incident response while allowing user intervention for key decisions.
Setting up the environment :
Windows machine:
To begin, I set up a Windows machine as an endpoint by spinning up an AWS EC2 instance with Windows Server. I chose minimal specs to keep it lightweight. After generating the necessary keys, I used Remote Desktop Protocol (RDP) to connect.
For the RDP connection, I used Remmina on my local machine. With the credentials provided by AWS, I connected to the Windows instance, and everything worked smoothly.
LimaCharlie:
I signed up for a free account with LimaCharlie and created an organization. To monitor the Windows machine, I added it to the platform by running the LimaCharlie agent directly on the machine. The command to install the agent was executed as follows:
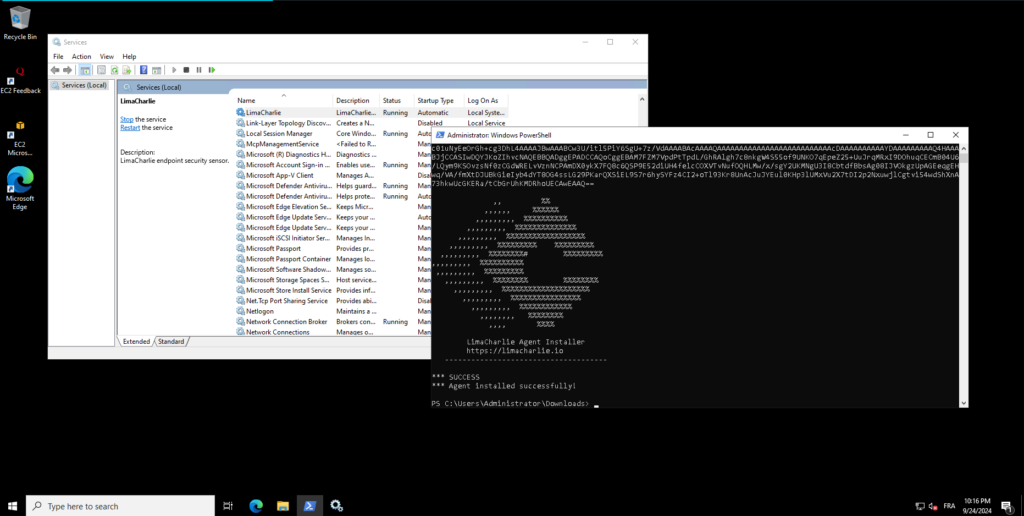
Once the agent was installed and running, the Windows machine appeared on our LimaCharlie dashboard under the Sensors list, confirming that it was successfully connected and being monitored.
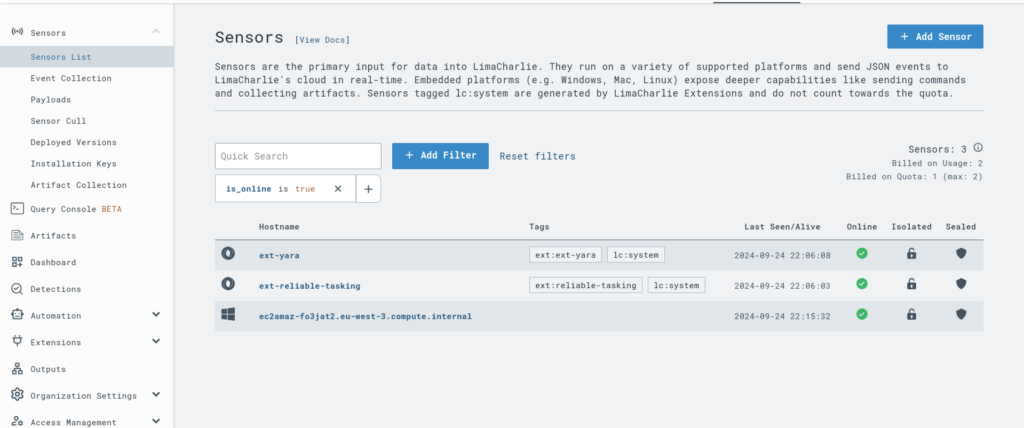
We can even run a netstat command directly from the EDR through LimaCharlie, which is pretty cool! This feature gives us a lot of flexibility, allowing us to gather network statistics and troubleshoot potential issues without needing direct access to the machine.
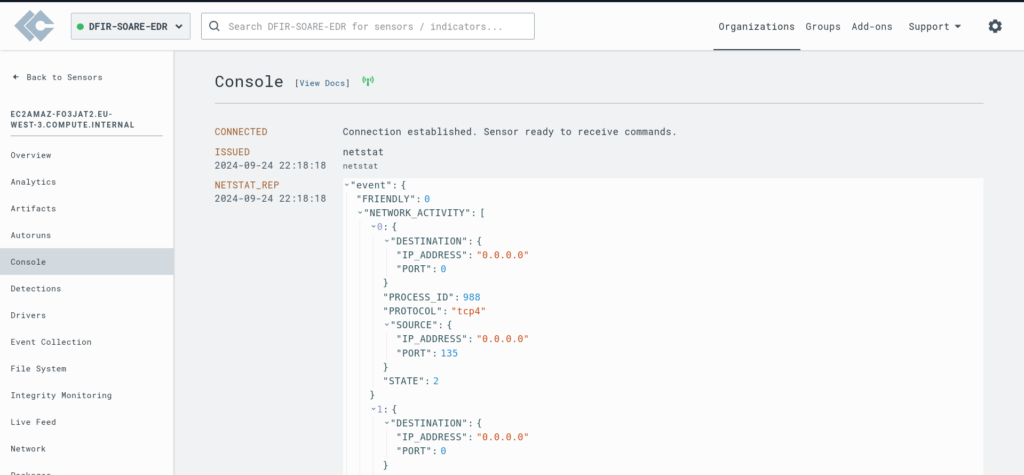
With LimaCharlie, we can do much more than just run commands like netstat. We have the ability to:
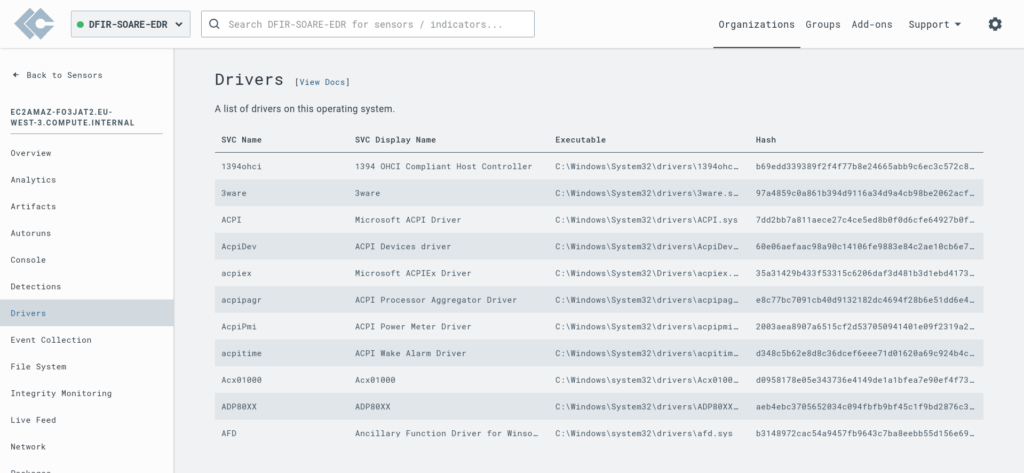
- Check installed drivers, ensuring nothing suspicious is running.
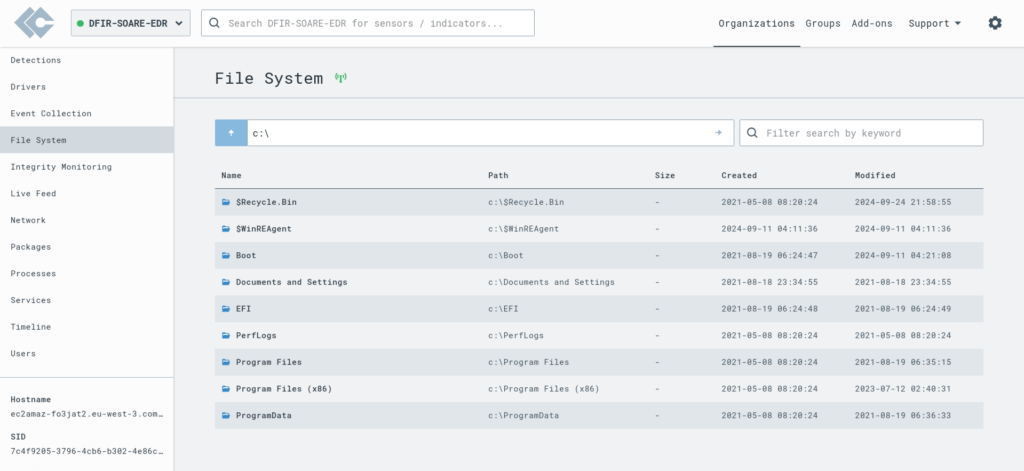
- Explore the file system, allowing us to inspect files and directories in detail.
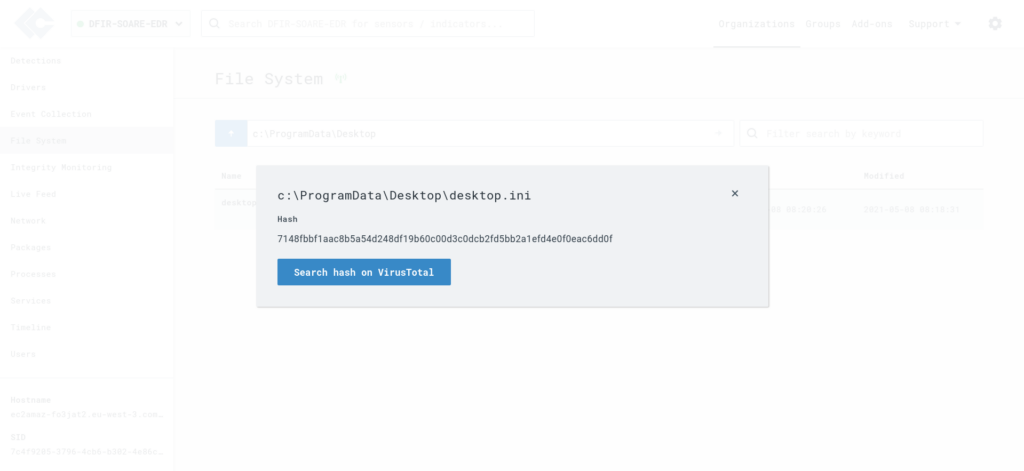
- Check file hashes on VirusTotal to quickly verify if any files are flagged as malicious.
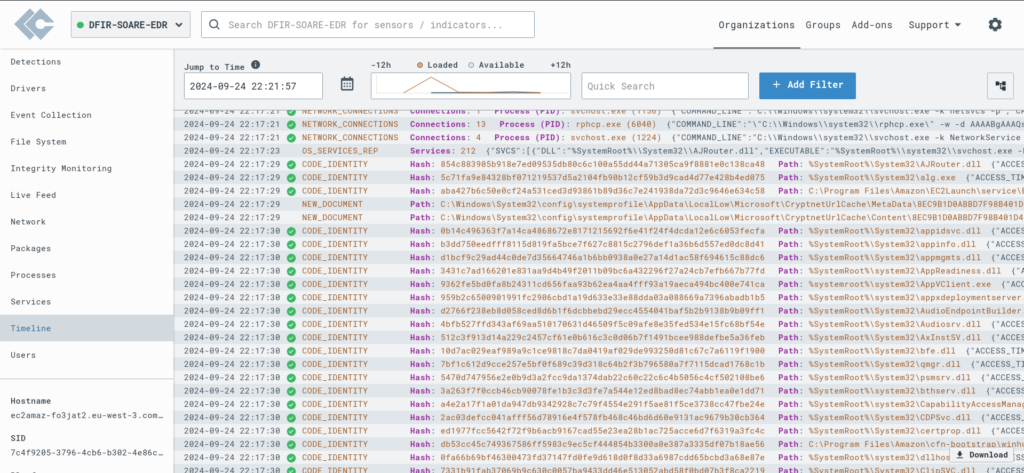
But perhaps the most interesting feature is the timeline view, where we can see the processes running on the machine in real-time, providing a clear picture of what’s happening at any given moment.
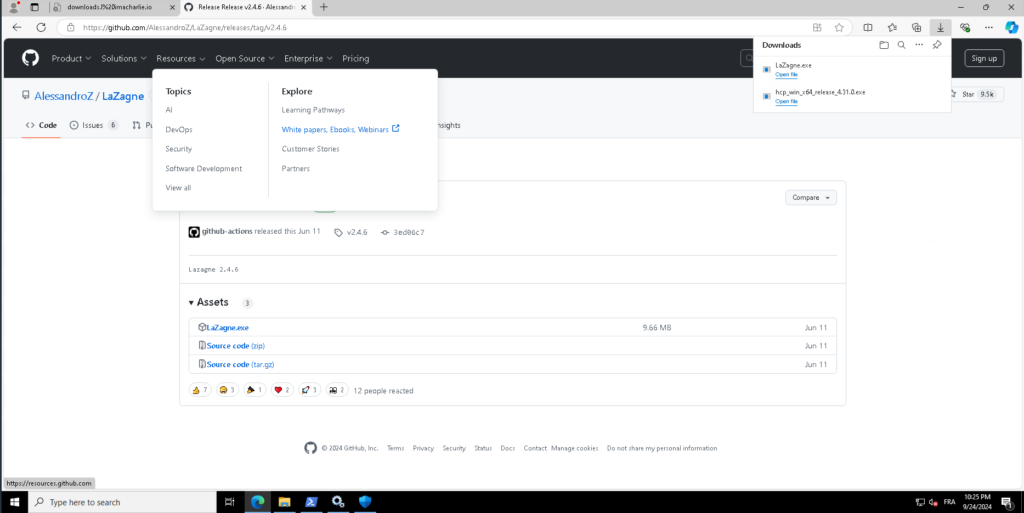
Installing LaZagne.exe
- Download: Visit the LaZagne GitHub repository to get the latest release of LaZagne.exe.
- Disable Windows Defender: Temporarily deactivate Windows Defender to avoid interference.
- Execute: Download the executable file and run it via PowerShell with administrative privileges.
Writing the detection rule
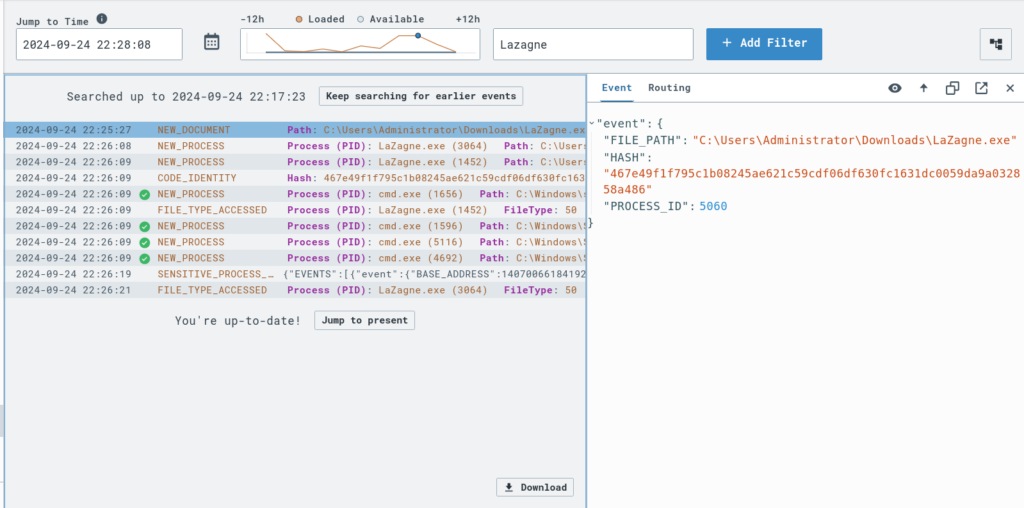
After executing LaZagne.exe on the terminal, the process immediately appears in the Timeline view of LimaCharlie as a NEW PROCESS. By clicking on this entry, we can access further details of the event, allowing us to monitor and analyze the execution in real-time.
We created a detection rule to identify the execution of LaZagne.exe. The rule is structured into two main components: detect and respond.
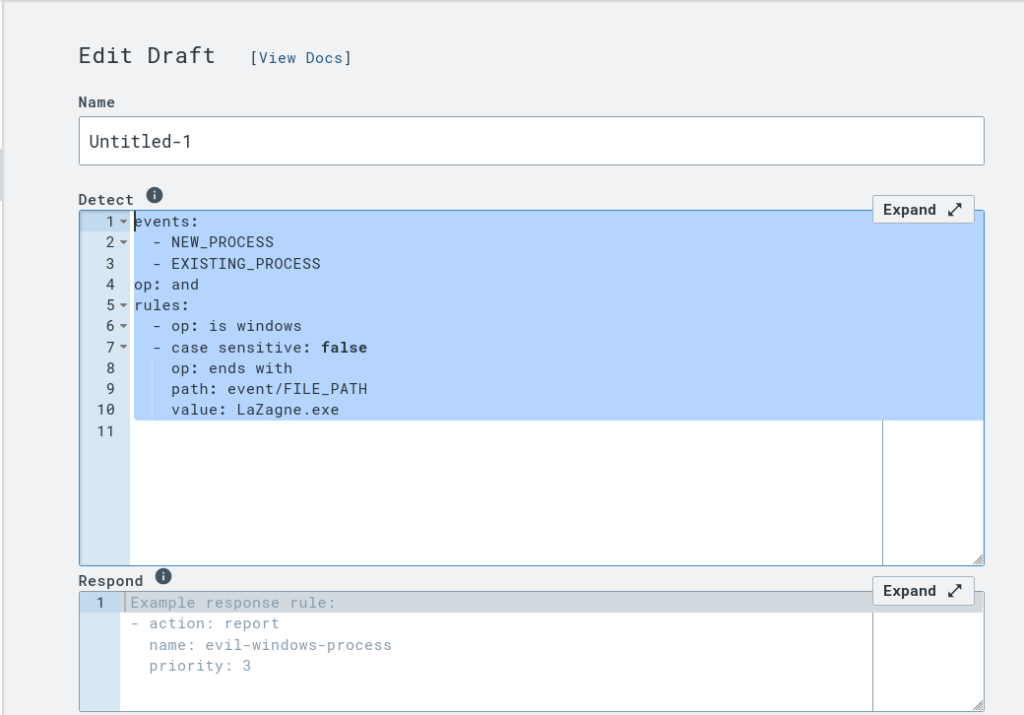
events:
- NEW_PROCESS
- EXISTING_PROCESS
op: and
rules:
- op: is windows
- op: or
rules:
- case sensitive: false
op: ends with
path: event/FILE_PATH
value: LaZagne.exe
- case sensitive: false
op: contains
path: event/COMMAND_LINE
value: LaZagne
- case sensitive: false
op: is
path: event/HASH
value: '3cc5ee93a9ba1fc57389705283b760c8bd61f35e9398bbfa3210e2becf6d4b05'
- action: report
metadata:
author: MyDFIR
description: TEST - Detects Lazagne Usage
falsepositives:
- ToTheMoon
level: high
tags:
- attack.credential_access
name: MyDFIR - HackTool - Lazagne
Explanation:
Events: The rule looks for both NEW_PROCESS and EXISTING_PROCESS events.
Detection Criteria:
The rule is applied specifically to Windows systems.
It checks if the process path ends with LaZagne.exe, if the command line contains LaZagne, or if the process hash matches the specified value.
Action: If any of these criteria are met, an alert is generated with the following metadata:
Author: MyDFIR
Description: TEST - Detects LaZagne Usage
False Positives: ToTheMoon
Severity Level: High
Tags: attack.credential_accessThis configuration ensures that any execution of LaZagne.exe is promptly detected and reported.
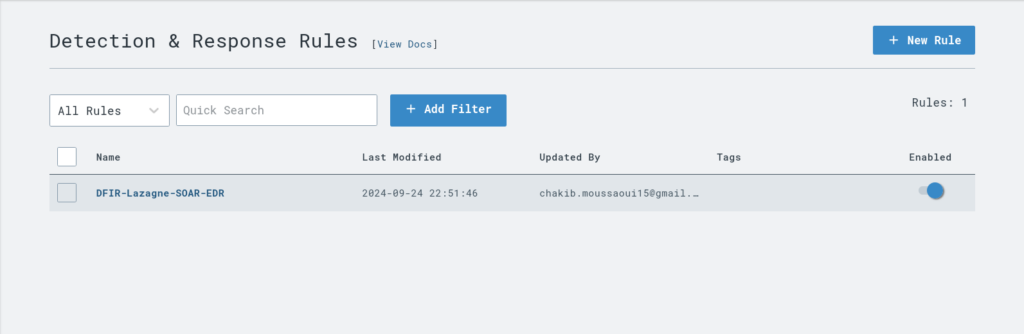
And here is our rule saved into our ‘Detection & Response rules’:
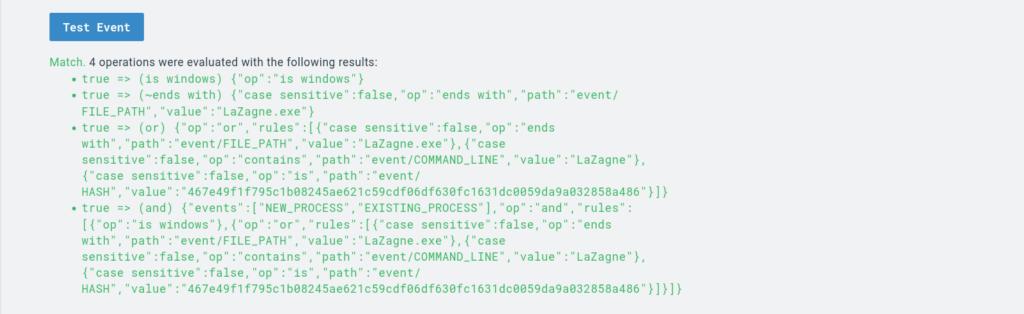
We can test the rule by pasting a sample event into LimaCharlie. The platform will then evaluate whether the rule correctly responds to this event. If the rule triggers the expected response, it confirms that the rule is correctly written and functioning as intended.
This testing feature ensures that our detection rule for LaZagne.exe is set up properly and will effectively identify such activities in real-world scenarios.
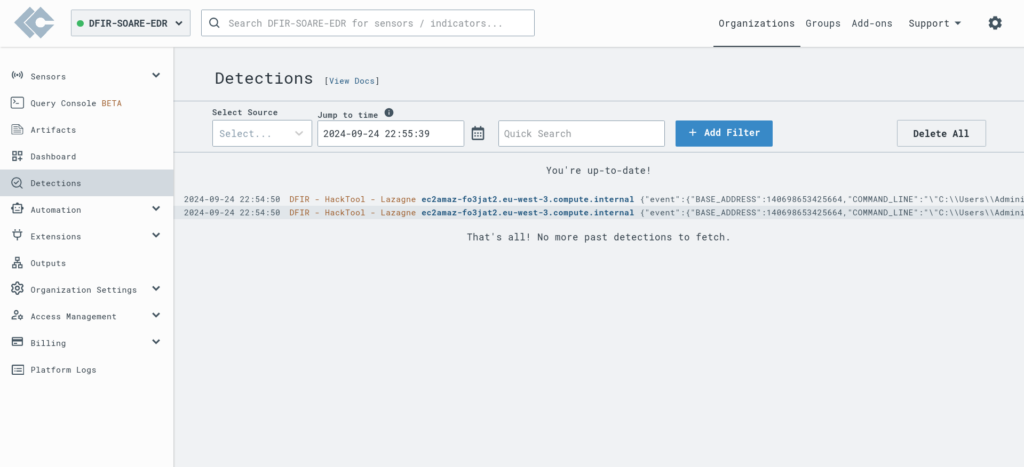
Setting Up the Output from LimaCharlie to Tines:
- Create Webhook in Tines: Set up a webhook option in Tines and copy the provided URL.
- Configure LimaCharlie: Paste the copied URL into the output section of LimaCharlie.
- Name the Integration: Give the integration a descriptive name.
Once these steps are completed, LimaCharlie will send alerts to Tines, enabling automated incident response based on the configured workflows.
Tines Playbook Setup:
- Webhook Data Forwarding: Configure the Tines playbook to forward data received from the webhook.
- Slack Integration:
- Use a LimaCharlie Slack template to send messages.
- Configure the channel ID within the template to ensure the message is sent to the correct Slack channel.
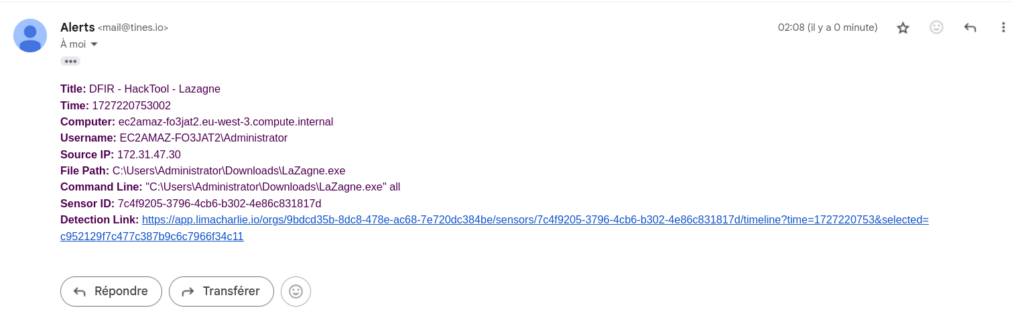
- Email Integration:
- Use a LimaCharlie Email template to send notifications.
- Configure the email settings, including recipient addresses, subject lines, and message content, within the template.
and it works !!
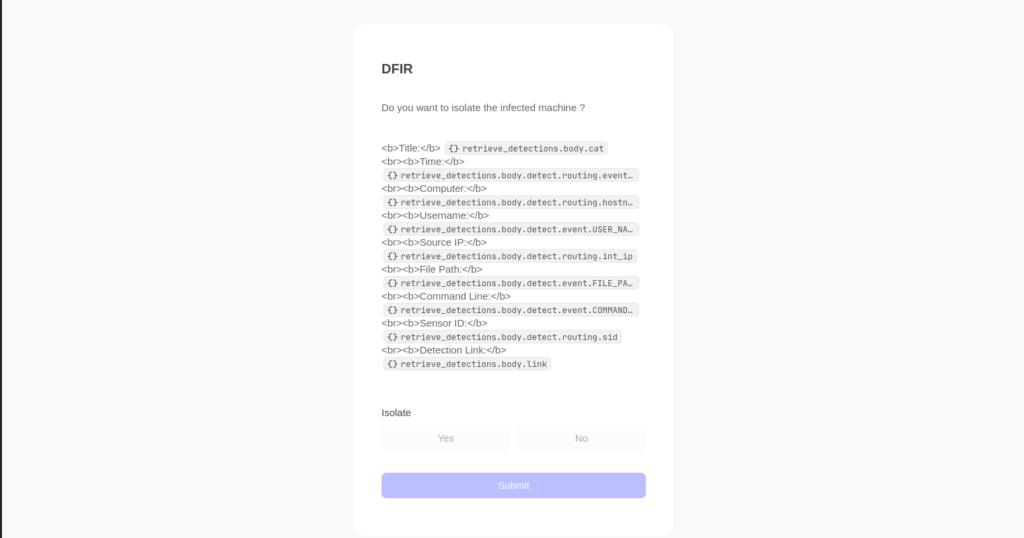
User Input Setup :
We created a page on Tines designed to take user input in the form of a boolean value to determine whether to isolate the machine. The configuration for this input is set as follows:
- Input Type: Boolean
- Options:
- Isolate:
true - Isolate:
false
- Isolate:
Trigger and LimaCharlie API Setup:
User Input Triggers:
- If
Isolateisfalse: Send a message to Slack stating, “Machine not isolated.” - If
Isolateistrue:
Use a LimaCharlie HTTP request template to isolate the machine by sending a request to the LimaCharlie API. Ensure the API credentials are correctly set up in Tines.
After the isolation request, send the isolation status to Slack, informing the team of the action taken.
Machine Isolation:
As we can see, we successfully isolated the machine remotely by responding to the prompt and sending the request. The entire process worked seamlessly, demonstrating the effectiveness of the automated workflow and integration between Tines and LimaCharlie.
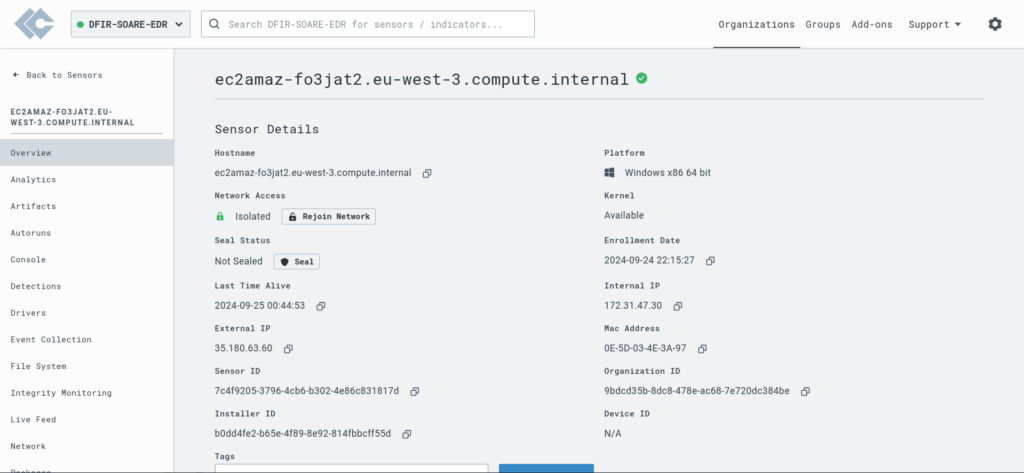
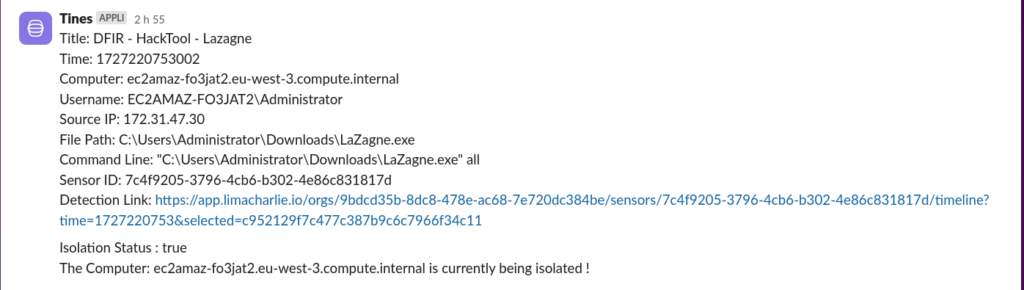
Final Tines Playbook Setup:
- Webhook Data Handling:
- Receive Data: Configure a webhook to receive alerts from LimaCharlie.
- Forward to Slack: Use the LimaCharlie Slack template to send notifications to the specified Slack channel.
- Email Notification:
- Send Email: Use the LimaCharlie Email template to notify relevant recipients via email.
- User Input Page:
- Prompt for Isolation Decision: Create a page that takes a boolean input (
true/false) for isolating the machine.
- Prompt for Isolation Decision: Create a page that takes a boolean input (
- Triggers Based on User Input:
- If
false: Send a message to Slack: “Machine not isolated.” - If
true:- Isolate Machine: Use the LimaCharlie HTTP request template to send an isolation command via the LimaCharlie API.
- Send Isolation Status: Notify Slack with the isolation status.
- If
The final Tines playbook should look something like this:
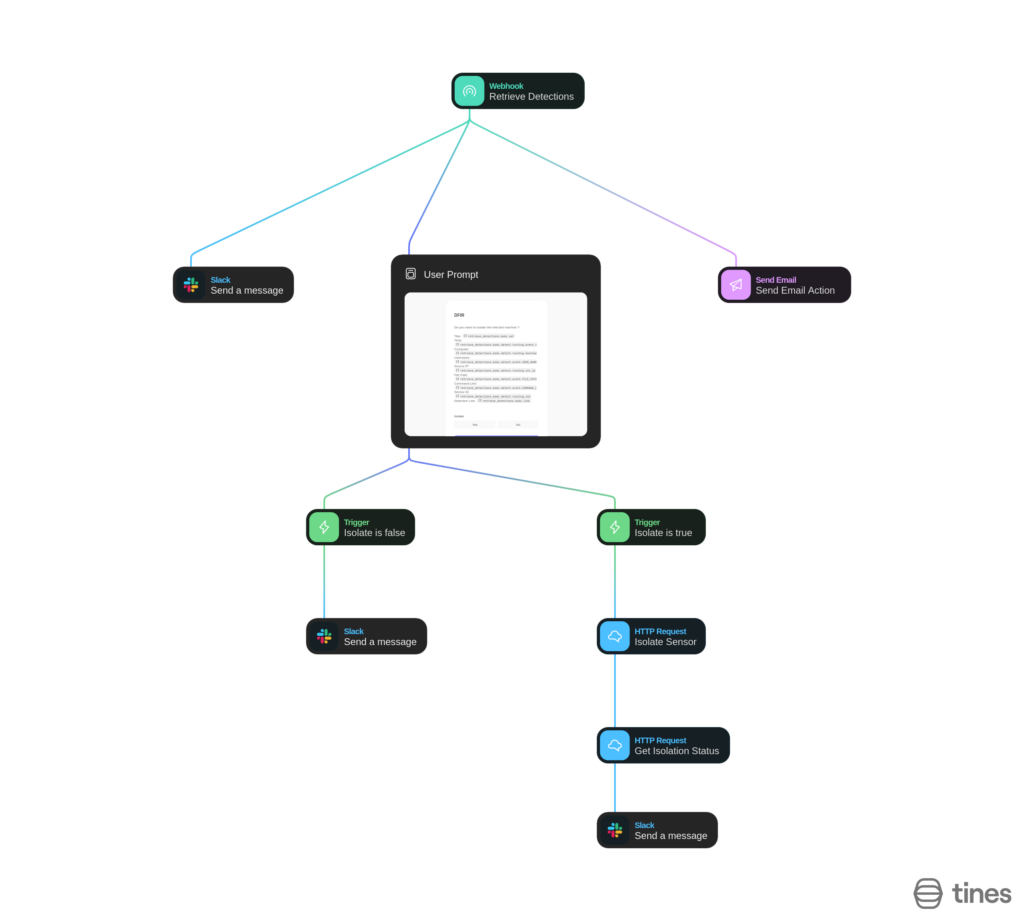
Conclusion and final thoughts:
I thoroughly enjoyed working with a real SOC problem and setting up this automated incident response system. It was exciting to see how integrating LimaCharlie with Tines can effectively address current cybersecurity challenges. This hands-on experience has only increased my enthusiasm for tackling such issues in real-world scenarios. I look forward to applying these skills and insights to make a meaningful impact in cybersecurity.